Page History
...
Property | Description |
|---|---|
LDAP Host | LDAP server hostname or IP address. |
LDAP Port | TCP/IP port that the LDAP server is listening on. Set this to 389 for normal LDAP connections, or 636 for encrypted connections (that is, if no custom changes have been to the LDAP configuration). |
| Encryption | The encryption method implemented by the LDAP server. (Options include: None, TLS, SSL) This determines whether or not the LDAP connection would need to be encrypted. |
LDAP Base Distinguishing Name (DN) | The LDAP node that all users and groups are contained within. All your users might not be contained within a single group, so set the base domain here. Yellowfin will start searching for the LDAP directory from here. |
LDAP (Yellowfin User) Group | LDAP Group Name that identifies which users have access to Yellowfin. This group exists in the LDAP directory, not Yellowfin. Only members of this group will be able to log in to Yellowfin. You can grant access to multiple LDAP groups, by using the ‘|’ character as a separator. For e.g: LDAP_Consumers | LDAP_Writers |
LDAP Bind User | The username of the user with the rights to search the LDAP directory. The format of this username should either be in NETBIOS or full domain. For example: admin@Yellowfin.bi or YELLOWFIN\admin Note: It is not recommended to use an admin user. |
LDAP Bind Password | The LDAP password required for the Yellowfin application to connect to the LDAP directory; it authenticates the LDAP Bind User defined above. You must click 'Update Password" before testing your settings. |
LDAP Search Attribute | This is a unique User Name field that LDAP users will log in to Yellowfin with. You can find the LDAP attributes by opening the property box of an LDAP object and clicking on the 'Attribute Editor' tab. You can set most of these attributes to a value of your choice. The attribute name is what you will provide in the LDAP Search Attribute field. |
LDAP First Name Attribute | This maps to the First Name attribute of the user within the LDAP directory. This is so Yellowfin can match the user to a name and create an internal user account. |
LDAP Surname Attribute | This maps to the surname attribute of the user within the LDAP directory. This is so that Yellowfin can match the user to a name and create an internal user account. |
LDAP Email Attribute | This maps to the email address attribute of the user within the LDAP directory. This is so that Yellowfin can match the user to an email address for broadcast reports. |
LDAP Role Attribute | This is an alternative method of mapping a Yellowfin Role to an LDAP user instead of the default role. By default, users brought in via LDAP will have the 'Consumer & Collaborator' role. But this sets a user’s role in Yellowfin in accordance to their LDAP directory prior to their login. See RoleCode in OrgRole table. Note that Role Attribute is an attribute of the user’s LDAP record. For example, in the LDAP directory, the user might be assigned an attribute called ‘YellowfinRole’ that contains the name of a Yellowfin role; the user will then be assigned this role upon logging into Yellowfin. |
| LDAP Group Filtering Criteria | Criteria used to filter a list of LDAP groups. Only groups returned in the filtered list will be passed to Yellowfin. |
| Ordering | This order in which internal authentication is performed. Options include: LDAP Authentication First (default) or Internal Authentication First. This setting is important as it determines how Yellowfin will authenticate a user attempting to log in. |
| LDAP group role mapping | This toggle enables functionality to associate LDAP groups with Yellowfin roles. Note that once enabled, it’s required that every LDAP user should only have one associated role. See here for a detailed process. |
...
- First, enable this functionality from the LDAP configuration page. Navigate to Administration > Configuration > Authentication page, and expand the LDAP Configuration tab (ensure that LDAP is selected as the chosen method of authentication)
- From this list of configurations, enable the LDAP group role mappingMap LDAP Group to a Yellowfin Role toggle.
- Save the changes.
- Navigate to the Admin Console, and from the Roles tab, select a role to associate LDAP groups with.
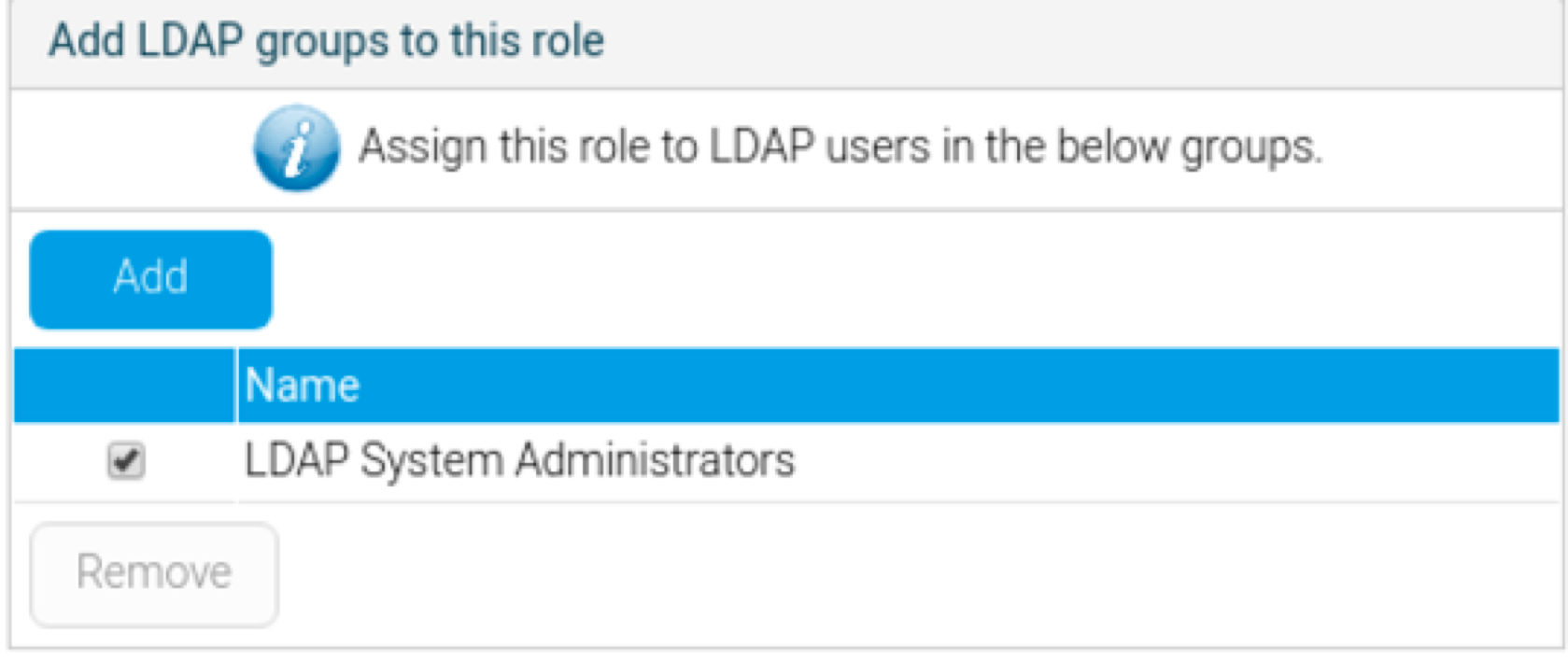
- At the Role page, scroll to the panel titled ‘Add LDAP groups to this role’ (this only appears if the LDAP group role mapping functionality is enabled).
- Add an LDAP group to associate to the selected role.
- Save the settings on the role page.
- Users of this LDAP group will now inherit all the role permissions defined directly here upon logging into Yellowfin.
...