For troubleshooting, it is better to run SSO URL provided by onelogin.saml2.idp.single_sign_on_service.url of onelogin.saml.properties. Ideally, on AD FS server.
You may see the error like
ERROR c.onelogin.saml2.authn.SamlResponse - Signature validation failed. SAML Response rejected
That means that the public key which you refer in onelogin.saml.properties is not valid:
onelogin.saml2.idp.x509cert =MIIC2DCCAcCgAwIBAgIQfdRAAWmWko1IsimA004o3TANBgkqhki…
Solution:
You may see this in Yellowfin logs:
org.apache.xml.security.encryption.XMLEncryptionException: Illegal key size
Original Exception was java.security.InvalidKeyException: Illegal key size
Solution.
When inspecting the SAML response payload below, the data is encrypted with AES-256:
EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes256-cbc"
By default, Java’s key size is limited to 128-bit key due to US export laws and a few countries’ import laws.
To fix:
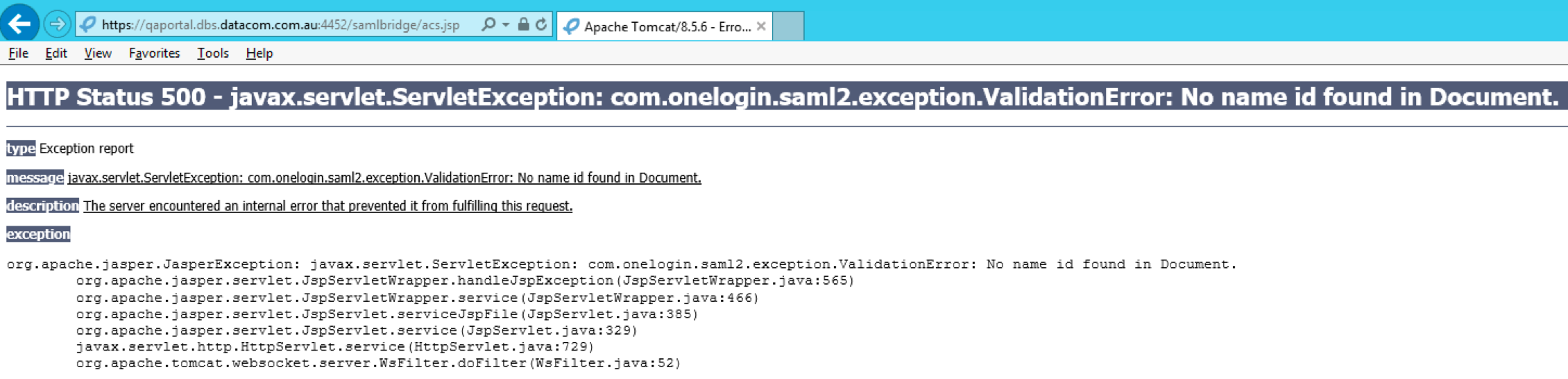
SAML requires name id as part of Identity Provider response. If you see in your browser something like

You do not pass correct name id from AD FS. Ensure that you pass correct name id from AD FS and the name id matches the format which SAML bridge expects (onelogin.saml2.sp.nameidformat of onelogin.saml.properties).
Possible formats:
NAMEID_EMAIL_ADDRESS = 'urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress';
NAMEID_X509_SUBJECT_NAME = 'urn:oasis:names:tc:SAML:1.1:nameid-format:X509SubjectName';
NAMEID_WINDOWS_DOMAIN_QUALIFIED_NAME = 'urn:oasis:names:tc:SAML:1.1:nameid-format:WindowsDomainQualifiedName';
NAMEID_UNSPECIFIED = 'urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified';
NAMEID_KERBEROS = 'urn:oasis:names:tc:SAML:2.0:nameid-format:kerberos';
NAMEID_ENTITY = 'urn:oasis:names:tc:SAML:2.0:nameid-format:entity';
NAMEID_TRANSIENT = 'urn:oasis:names:tc:SAML:2.0:nameid-format:transient';
NAMEID_PERSISTENT = 'urn:oasis:names:tc:SAML:2.0:nameid-format:persistent';
NAMEID_ENCRYPTED = 'urn:oasis:names:tc:SAML:2.0:nameid-format:encrypted';
Correct Yellowfin logs regarding to SAML response:
DEBUG c.onelogin.saml2.authn.SamlResponse - SAMLResponse validated --> …
…
DEBUG c.onelogin.saml2.authn.SamlResponse - SAMLResponse has NameID --> john.smith@yellowfin.bi
DEBUG c.onelogin.saml2.authn.SamlResponse - SAMLResponse has attributes: {http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress=[john.smith@yellowfin.bi]}
DEBUG com.onelogin.saml2.SamlAuth - processResponse success --> <very long line representing signing certificate>
If you see this in Yellowfin logs:
INFO (AdministrationService:remoteAdministrationCall) - WebserviceException caught: 8(COULD_NOT_FIND_PERSON)
That means that you switched the user provision off and this id is not a Yellowfin user.