Yellowfin exposes a public REST API that allows third party developers to create their own utilities, applications, and integrations with Yellowfin systems and content. This can work in tandem with existing integrations such as the JS API, SOAP API, and tight application integration, or as an entirely standalone integration tool.
The API exposes most features of several main content types such as stories, signals, discussion streams, reports (coming soon), users, and user timelines. It also has some administration capabilities to supply features such as user management, category management, import/export, system configuration, and user session management so that developers can provide their own utilities to administer and control their Yellowfin system.
Some of the possible uses of the API are to:
The REST API is available under the /api namespace. For example, https://yellowfin.myapp.com/api/stories
Additionally, the suite includes RPC (Remote Procedure Call) endpoints which support workflows that are difficult to fit into the REST paradigm. These are located in the /api/rpc namespace.
Every API request requires an Authorization header. Its format is YELLOWFIN ts=1600224140615 nonce=3370ddc4-37d9-41b9-9f24-ada181fdc4bf token=securityToken
| Component | Description |
|---|---|
YELLOWFIN | Custom authentication scheme. This text should match the application name, which can be set via the custom installer properties file or via Yellowfin configuration database. Note: the text must be written in uppercase, without any spaces. For example, if the App Name is 'BigFish Reporting' instead of 'YELLOWFIN', the authentication scheme should be written as 'BIGFISHREPORTING'. |
ts | The time in milliseconds from the Unix epoch 00:00:00 UTC on 1 January 1970. This is the current time in the program which calls the API. Every programming language has a way to get the current time in this format. |
nonce | A random UUID generated by the client. |
token | A security token used for authenticating the user and authorizing access to the resource. Not all endpoints require this section, since some can be accessed without authorization (see documentation). |
Every API request requires an Accept header.
application/vnd.yellowfin.api-v1+jsonThere are two security tokens which are key for consuming the API.
| Token | Description |
|---|---|
| Refresh | This is an opaque security token obtained on login. Refresh Tokens do not expire and may be securely saved in the client application for obtaining access tokens. |
| Access | This is a JSON Web Token (JWT) which expires after 20 minutes. An access token needs to be sent in the Authorization header of nearly every API request. On expiry, the client application can use the refresh token to get a new access token. |
Every API response will have one "_links" object. The "_links" object can also contain one or more link objects.
"href" attribute to access the resource rather than hard coding it in application code."options" array lists the HTTP methods which the user is authorised to use with the link. For example, the example above tells us that the user can read the comments list (GET) or create a new one (POST). They cannot delete all comments, which is why DELETE is not available in the "comments" link.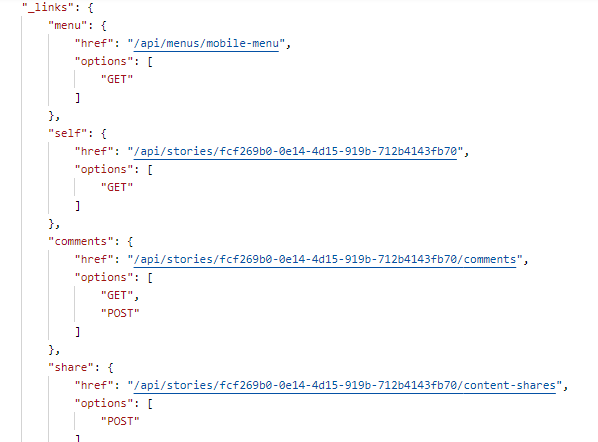
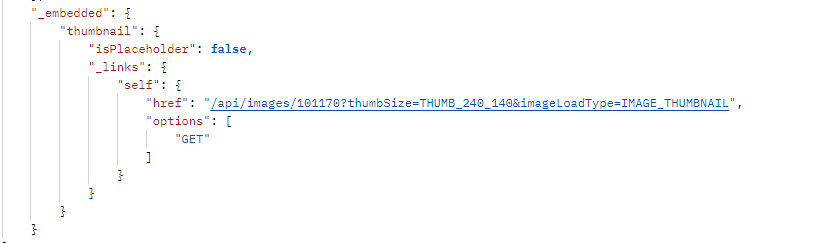
Some API responses will have an "_embedded" object, which can contain sub-objects that contain additional useful information related to the current resource, but which does not belong directly to that resource. These are separate resources which can have their own properties and links.
Most endpoints in the API require authentication. Some notable exceptions are:
/api resource, which can be used with or without authentication to get basic api info generally used by the api-consumer application; and,The REST API uses refresh tokens and access tokens to authenticate and authorize access to resources. These tokens can be generated in a few different ways.
The standard login flow passes user credentials to the server to authenticate and generate a refresh token, and as a convenience also an access token. The refresh token can then be used to create access tokens, which can be used to access other resources.
Rather than a session, a refresh token is used to identify a user. A consumer must create a refresh token and obtain an access token before they can use other REST endpoints. Creating a refresh token can be thought of as a login process.
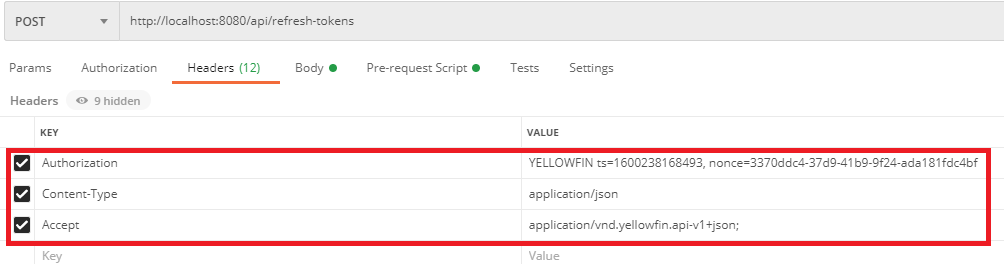
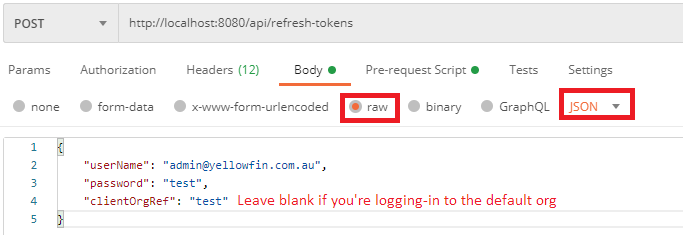
_embedded property, an access token.
The client application should securely store these tokens. It should also store the "self" link as it will be needed for logging out. |
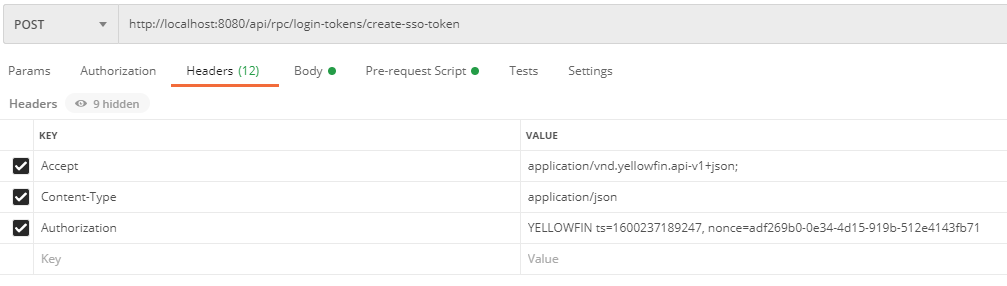
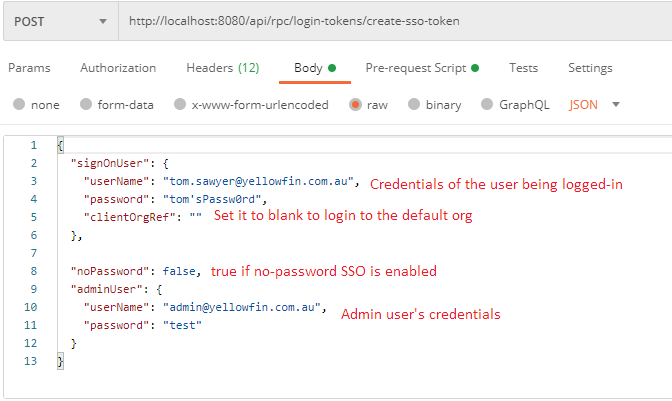
The API provides single sign-on (SSO) functionality within the REST API itself. This allows a REST user to logon another REST user, generating a refresh token for that user, which can be forwarded on to that user (or more likely another application) to allow use of the API. This endpoint supports inline authentication for the REST user who is making the SSO request, and supports simple authentication (see the Troubleshooting note below about SSO errors with noPassword SSO).
This is essentially another form of SSO that can be done from the web application. Administrators can generate onboarding tokens for specific users to be passed to an external application that can then pass that token into their authentication flow rather than requiring the user’s credentials to generate a refresh token. If a token is passed with a refresh token POST request (and it’s not a normal REST SSO request from above), then this token is verified against the token created in the web application to logon the user.
Both the web application and the JavaScript API use a different token system to handle single sign-on, which means that you cannot use these tokens interchangeably. Thankfully, the REST API provides several ways to generate the Web SSO tokens required (called login tokens in the REST API). There are three main ways to generate one of these tokens.
Generation method | Description |
|---|---|
Generate a token for any other user while logged in | Passing a user’s credentials in the request to /login-tokens will authenticate that user and create a Web SSO token for that user. This can be used by an admin account to logon other non-admin users. |
Generate a token for the current logged-in REST user | This uses the same flow as above, but if no secondary user credentials are passed, then a token is generated for the current user instead. This is useful for integrations to redirect the current user to JS API or web content. |
Generate a token for any other user while not logged in | Using the /rpc/login-tokens endpoint allows the use of inline authentication to pass both an admin user’s credentials as well as the credentials of the user to be logged in. |
A popular use-case for the API is Web SSO. A couple of API endpoints are available for generating a login token. The generated token can be used to login to Yellowfin’s browser interface. The simplest way to do this is to use the RPC endpoint POST /login-tokens/create-sso-token.
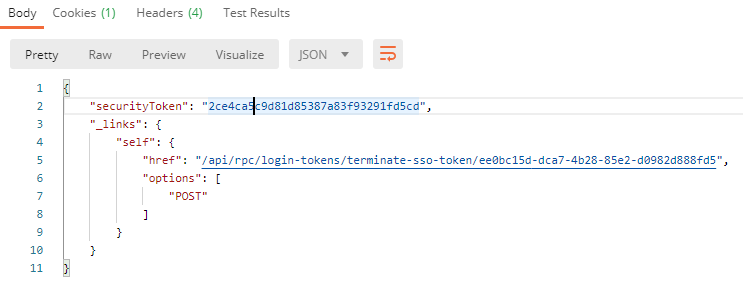
Creating an access token is a very similar process to creating a refresh token. To create one:
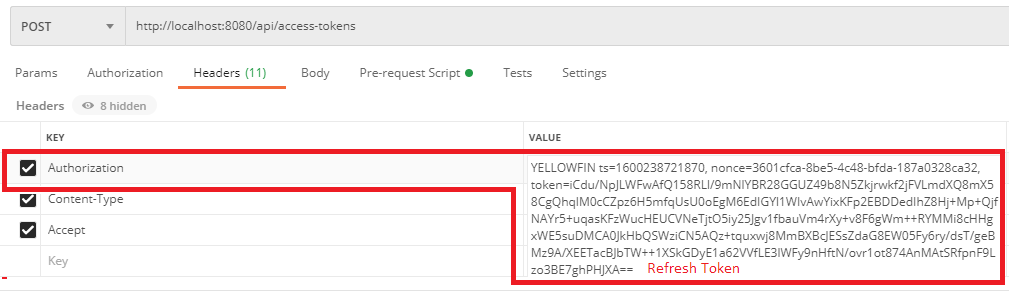
The refresh token response provides an access token to make it easier to start consuming the API after login.
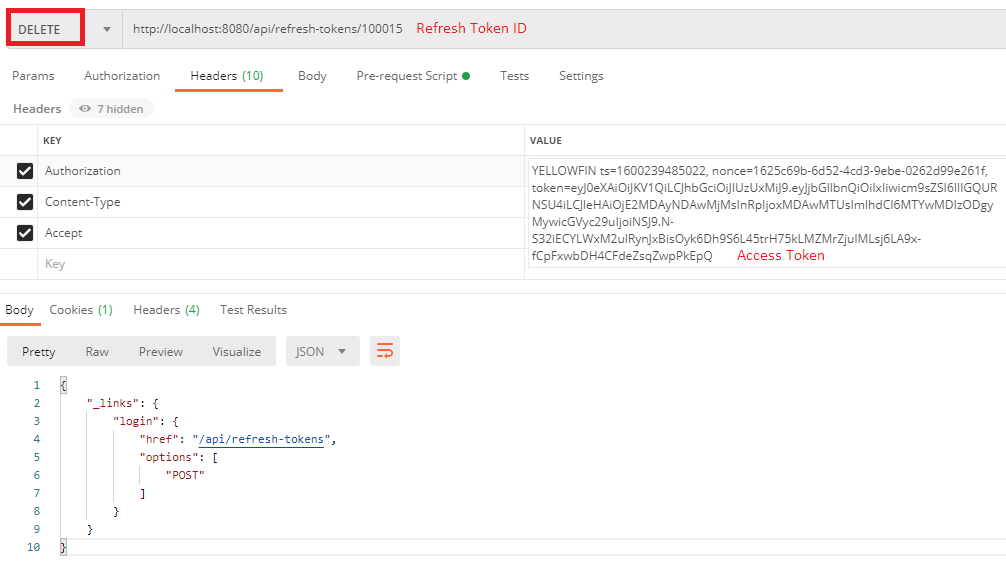
Any logon flow that results in a refresh token being generated can be logged out in the same way. Single log-off (SLO) can be achieved by passing another user’s token ID to be deleted by the /refresh-tokens endpoint as long as the currently logged-in user has rights to do so.
It is also possible to SLO a Web SSO session by passing the token ID (returned when the login token was created) to the /login-tokens DELETE endpoint. The same access restrictions apply.
The response of the POST/refresh-tokens request will contain the information required to effectively "log out" of the REST API — a call to delete that refresh token. The response of the POST/refresh-tokens request contains a _links property.

The options array in the "self" link lists which operations can be performed on the new refresh token. There should only be one — "DELETE". Calling DELETE /refresh-tokens will effectively log the user out of the REST API.
Note that a valid access token is required to perform this operation. It must be included in the token property of the Authorization header.
Please consult the API doc for the headers that need to be specified for each endpoint, along with mandatory and optional parameters. Please consult the API doc for the headers that need to be specified for each endpoint, along with mandatory and optional parameters.
This endpoint describes the current state of the API itself, represented as a standard REST resource. It is available to both logged-in and non-logged-in users, so it can be accessed with or without an access token. It returns API information such as the current API version, server information such as the current application version (see note below). The endpoint also returns all the top-level resources that are available to the current user (if no user is logged in, it returns the top-level endpoints which can be accessed by a user who is not logged in).
Sometimes available endpoints can differ between application versions for the same REST version, so it is important to pay attention to this value as well as the API version. |
Almost all standard resources require access token authentication, and are mostly represented as JSON (see the REST API documentation for endpoint specifics). These generally share a standard structure with object properties as well as _links, and _embedded properties for navigation and additional useful information.
Most list endpoints implement a filtering system that uses JSON-serialized objects to pass filtering information to the endpoint. These endpoints are also generally accompanied by a direct child /metadata resource which describes the filter values available to the current user. See the REST API documentation for each endpoint for more information.
There are several endpoints that provide a fields parameter, which can control which model fields are returned in the API response. These are sent as a serialized JSON list of property names that should be included. This feature is not uniformly implemented across all endpoints, and not all fields are able to be excluded on all endpoints. See the REST API documentation to find the details for each endpoint.
RPC (remote procedure call) endpoints are similar to standard resource endpoints in that they follow the same rules for authentication (some RPC endpoints have inline authentication; see the REST API documentation) and response structures, but which do not follow the REST paradigm. Instead of representing a resource directly, these represent a procedure to be run on the server. All RPC endpoints use the POST operation.
The reason these exist is that they implement features that are very difficult to fit into the REST paradigm, such as endpoints which require stateful interactions, or complex multi-request call structures. These generally are features that have been migrated from existing SOAP services or the web application interface and are very difficult to refactor cleanly. Some of these features may be converted to a fully RESTful implementation in future.
Most endpoints that have a POST operation available require passing parameters in the request body, unless they are simple enough that they do not require any additional parameters. There are two main situations which can cause the required format of the request body to differ:
Please see the REST API documentation for the exact requirements of each endpoint.
In general, most use cases of the API are going to need to follow a similar approach to logging in to the REST API. This approach constitutes the initial connection and user login to the REST API. Please note that subsequent connections will not need to generate another refresh token unless the token has been invalidated by a user- or administrator-forced logout. In the case of applications that support features that may be ahead of some servers, it’s a good idea to check that the version of the server has not changed between sessions.
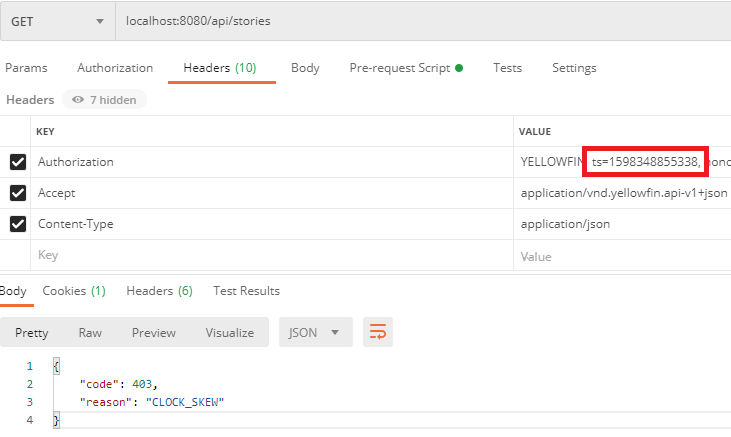
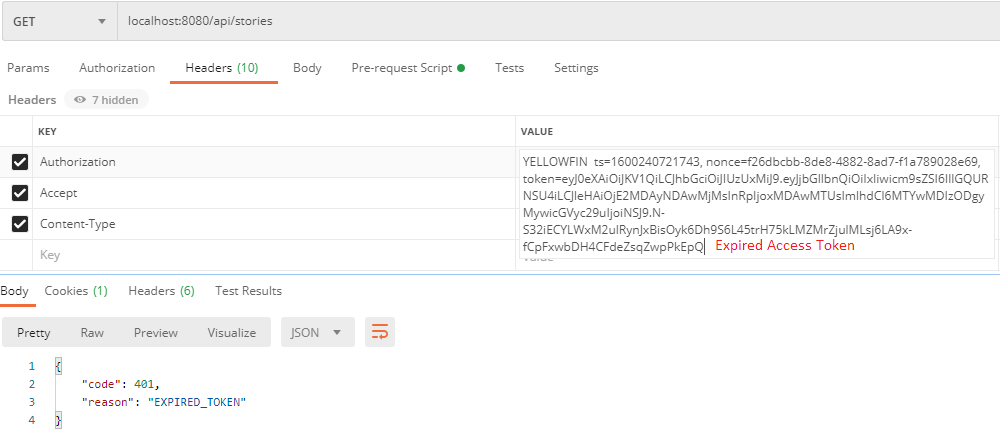
Accept header.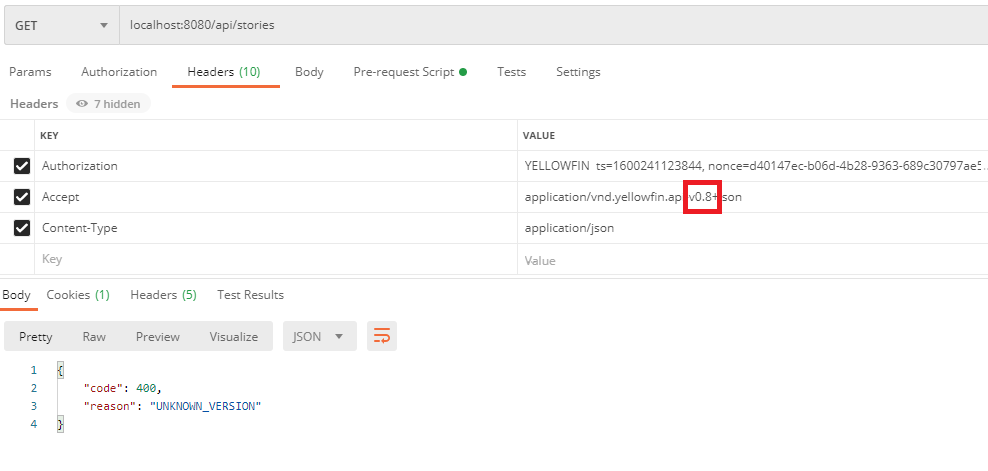
noPassword authentication is being used, ensure that it has been enabled on the server. This is done by inserting a record into the Configuration table and restarting Yellowfin.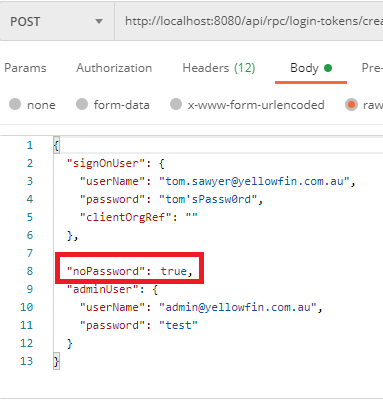
The full documentation of the current REST services is available in our external developer site. Click here to access it.